The frequency and strength of Distributed Denial of Service (DDoS) attacks is on the rise. Through the exploitation of millions of insecure Internet-of-Things (IoT) devices, the creation of botnets waging highly distributed volumetric attacks is easier and more impactful than ever before. In addition to larger attack volumes, efforts are shifting from the network and transport layers to the application layer (layer 7). Application layer attacks are far more sophisticated, often requiring fewer resources to bring down a website or application, and can disrupt operations with even greater impact.
DDoS attacks disrupt normal business operations by degrading website and application performance and availability, sometimes knocking them offline completely. The average hourly cost of downtime due to an infrastructure failure is $100,000 per hour. Attacks of this nature likely lead to customer churn, brand degradation, and lost business.
Websites and applications require the resilience and intelligence of a scalable network to combat the biggest and newest attacks. Protecting against threats should not degrade performance caused by security induced latencies and security services must be easy to configure to eliminate misconfigurations, which introduce new vulnerabilities.
Contact Our Team
+1 (888) 565 7668
Related Products
DDoS Protected VPS DDoS Protected Dedicated Server DDoS Protected CDN Remote Network DDoS Protection Colocation

Defend against the largest attacks
Our network capacity is 15x bigger than the largest DDoS attack ever recorded. With 15 Tbps of capacity, it can can handle any modern distributed attack, including those targeting DNS infrastructure.

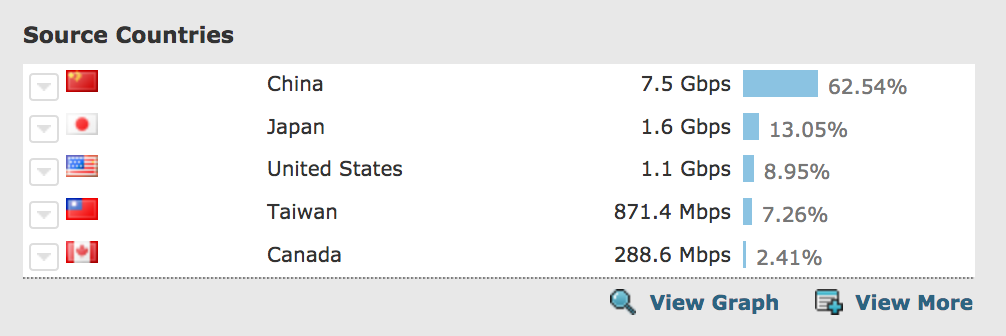
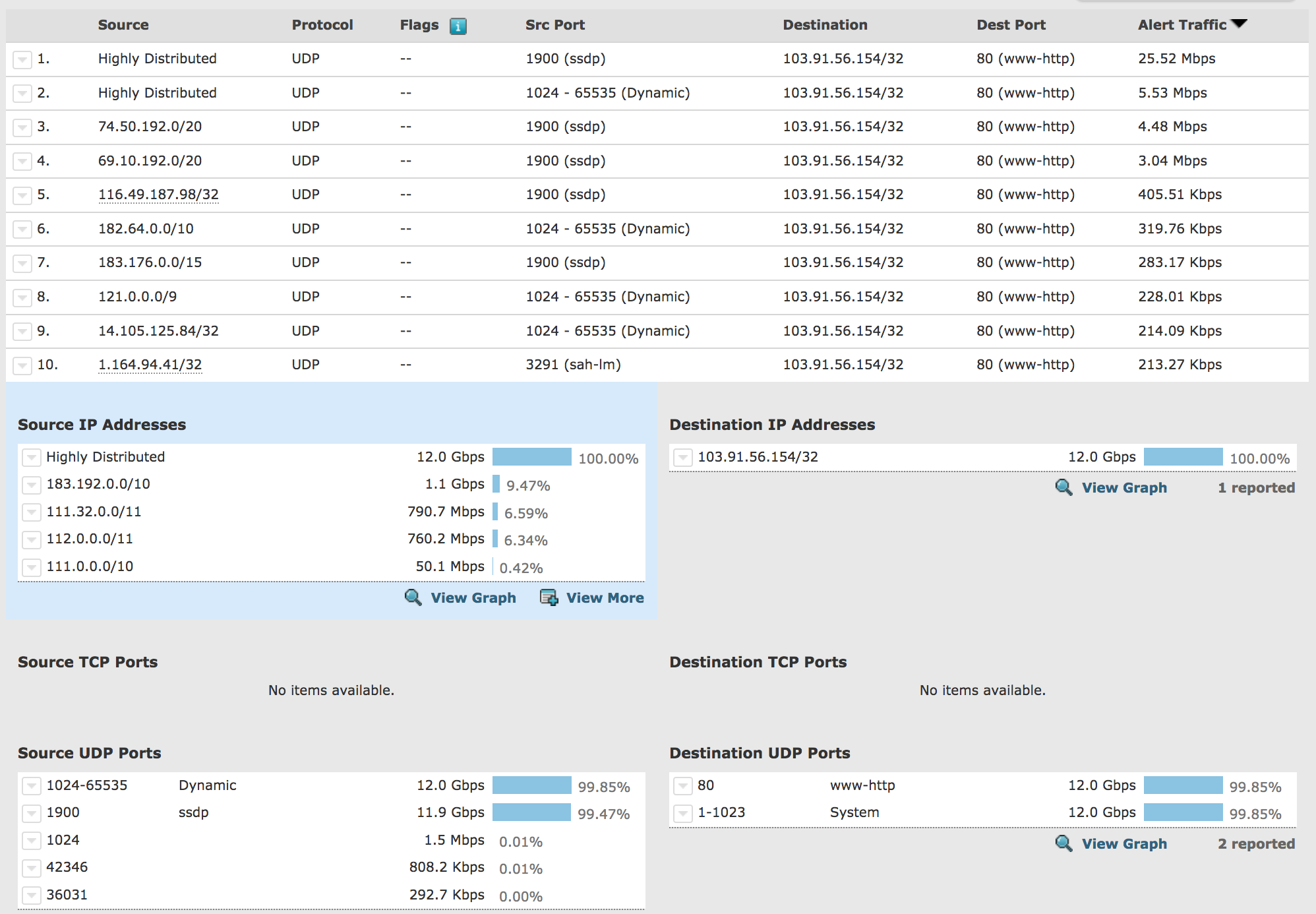
Shared Network Intelligence
With every new property, our network becomes smarter. our IP reputation database identifies and blocks new and evolving threats across all 7 million properties on the network.

No Performance Tradeoffs
Eliminate security induced latencies by integrating with KVM.NET’s included performance services, including CDN, smart routing, website optimizations, and the latest web standards.
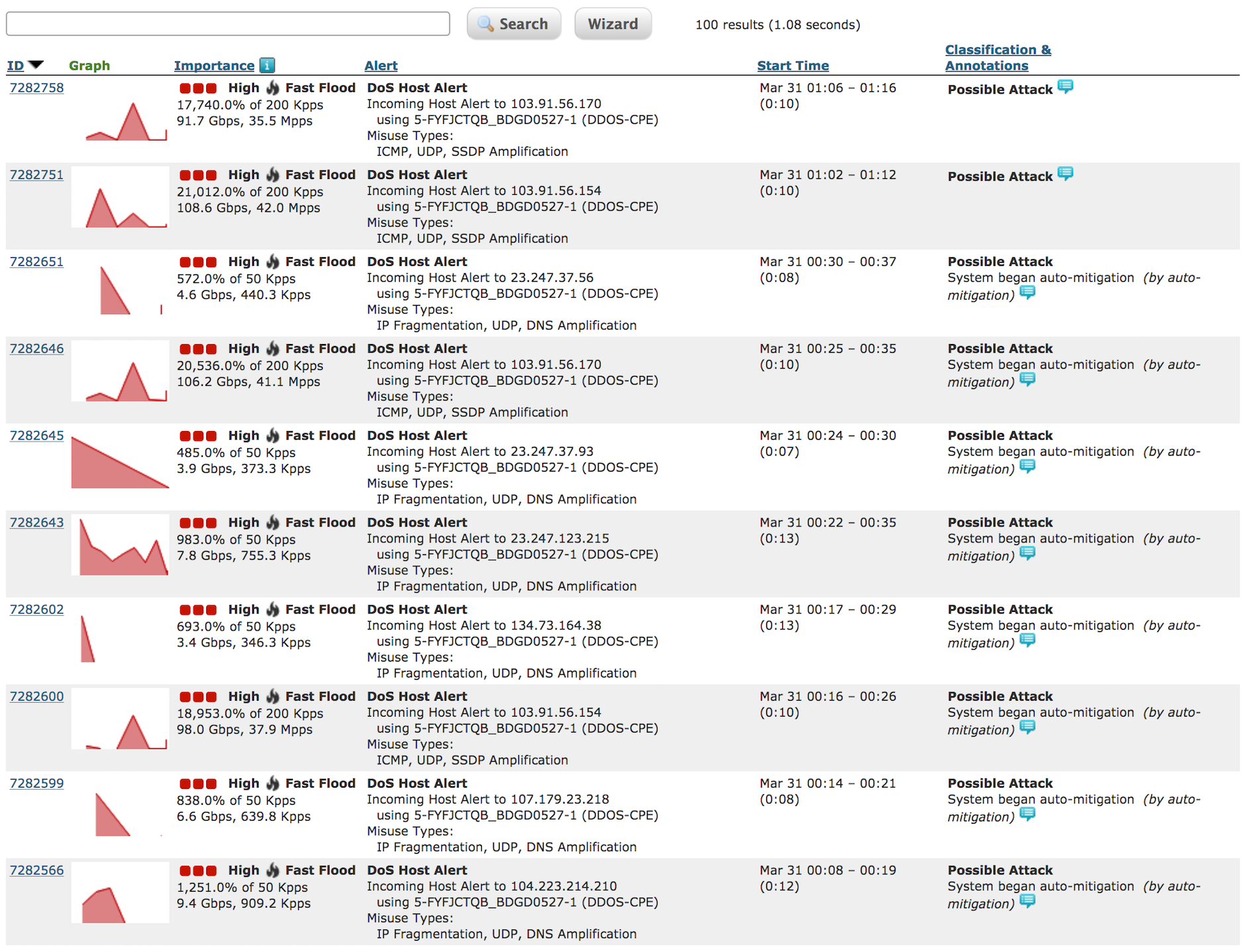
Common Types of DDoS Attacks

DNS Flood
By disrupting DNS resolution, a DNS flood attack will make a website, API, or web application non-performant or completely unavailable.
UDP Amplification (Layer 3 & 4)
An attacker leverages the functionality of open DNS or NTP resolvers to overwhelm a target server or network with amplified request traffic, where the payload size is greater than the size of an originating request.


HTTP Flood (Layer 7)
HTTP flood attacks generate high volumes of HTTP, GET, or POST requests from multiple sources, targeting the application layer, causing service degradation or unavailability.
Layered Security Defense
KVM.NET’s layered security approach combines multiple security capabilities into one service. It prevents disruptions caused by bad traffic, while allowing good traffic through, keeping websites, applications and APIs highly available and performant.

KEY RESULTS
750Gbps
attacks blocked between February 2018 and March 2018 — 500,000 attacks per day — and not one was successful.
95%
total monthly bandwidth savings.
Cloud-DNS
"We run an Authoritative DNS Cluster over 20k domain name The Mitigation is Spotless and The KVM.NET is a trusted DDoS Protected provider."
Trusted by 150,000+ websites
Features
KVM.NET's Performance and Security Services work in conjunction to reduce latency of web sites, mobile applications, and APIs end-to-end, while protecting against DDoS attack, abusive bots, and data breach.

Content Delivery Network (CDN)
With 10 data centers, KVM.NET’s Anycast CDN caches static content at the edge, reducing latency by delivering assets as close as geographically possible to visitors.

Website Optimizations
Includes a suite of web optimizations to improve the performance of Internet assets. Optimizations include the latest web standards, such as HTTP/2 and TLS 1.3, as well as proprietary enhancements for images and mobile device visitors.

Anycast Network
With 10 data centers and 4.5 Tbsp of capacity, Our Anycast network absorbs distributed attack traffic by dispersing it geographically, while keeping Internet properties available and performant.

Web Application Firewall (WAF)
Enterprise-grade web application firewall (WAF) detects and block common application layer vulnerabilities at the network edge, utilising the OWASP Top 10, application-specific and custom rulesets.

SSL / TLS
Transport Security Layer (TLS) encryption enables HTTPS connections between visitors and origin server(s), preventing man-in-the-middle attacks, packet sniffing, the display of web browser trust warnings, and more.

Access
ecure, authenticate, and monitor user access to any domain, application, or path on CDN.










 Pankaj Moon
Pankaj Moon